The ways of finding subdomains in minutes

Are you ready to implement what you have learned till now? After reading this, you’ll be a pro in finding subdomains of any domain. If you’re following the roadmap, congratulations you have finally made it to
Step 1 of penetration testing: Finding Subdomains

I’m as excited to share as you are to read, but first things first. Have you completed what was last discussed? Completed that if not before you move ahead because skipping won’t help to learn and you can subscribe too for the newsletters, I’ll be making your every weekend exciting by sharing new articles published in the week.
What is a domain?
Choose a target you want to practice with this article say Facebook. How would you reach Facebook from a browser? By typing facebook.com or fb.com, right? What you typed is called domain. Now, if you try to open a Facebook link on mobile, it generally opens m.facebook.com. This m here is the subdomain. Similarly, Haox(me — haox.illued.space) is a subdomain of Illued Space( illued.space). A domain can have any number of subdomains. So, say if you are testing for Facebook. All the Facebook subdomains will be part of your testing like developers.facebook.com, m.facebook.com, code.facebook.com, etc. Let’s know how to find the subdomains of a domain.
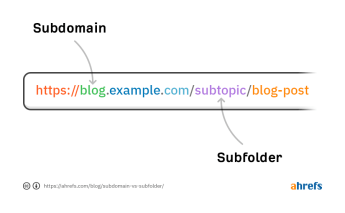
How to find subdomains?
There are 2 ways to do this. One is using your hands, brain, and focus, i.e, manually, and the other is by using a tool. I’ll share both one by one.
1. Manual — Google Dorking
If you are following the roadmap, you would know what Google Dorking is. This is what makes every developer a hacker. It may seem like a too simple thing, but don’t underestimate it. It’s the power that everyone has but only a few know the worth of it. You can find free ebooks, pdf, movies, series, and much more by understanding its worth. In this article, I will not be explaining Google Dorking, we’ll talk about only usage. To know how to use Google Dorking, read this.
So, how this will help here? Type this in your Google Search:
site:facebook.com -inurl:wwwWhat we did here is we asked Google to return results from facebook.com but exclude results that are on www.facebook.com website. Now, Google will show us results from various subdomains excluding its main domain(www.facebook.com). List them down.
2. Using Tool
- Open Terminal in Kali Linux.
- Install sudo apt install python3-pip
- Then, run these following commands
git clone https://github.com/aboul3la/Sublist3r.git pip install requests pip install argparse pip install dnspython cd Sublist3r git clone https://github.com/rthalley/dnspython cd dnspython sudo python3 setup.py installWhat we did here is we installed python and some libraries required. Then, we clone a git repository Sublist3r, whose work is to find subdomains of a domain automatically from various sources. If you want to know about what is sudo, cd, etc, read that here. Like I had shared, this article is about using the knowledge we gained till now, we are mixing all things up and trying that out. It’s time to get the subdomains now. For that run the following commands:
cd .. python3 sublist3r.py -d facebook.comIn no time, it will start listing the subdomains.

Sublist3r is an amazing tool, but you should know how to find it manually. So, here comes the -
To-Do
- Practice finding subdomains manually
- Learn more about Sublist3r or any better tool you find.
- Practice it using a target.
While you do this remember the caution,
CAUTION: You need to make sure that you will not use this information for any illegal purposes. This information is being shared for educational purposes only. If you find something sensitive while practicing this, do not use that information instead inform the website owner as soon as possible.
What I have shared are just 2 ways to find subdomains. There are many such, if you know or use any tool for this, do share in the comments below.
I’ll be back with another article sharing more techniques soon. Till then, keep practicing and stay tuned 😉!



