3 exclusive ways to bypass Cloudflare

When Cloudflare push code, it automatically affects approximately 25 million Internet properties and hence, sometimes things goes down all over.
Is your target using Cloudflare? No problem, this roadmap has got the solution for you — bypass Cloudflare. If you have reached here following the roadmap, you have got immense patience and self-motivation! Keep that high! This article is my contribution to help to increase your motivation.

Cloudflare owns and operates a huge network of servers. It uses these to help speed up websites as well as protect them from malicious attacks. It’s an absolute package of Analysis, speed, DNS, Security, etc. It gets complex when DNS grows and records changes.
Behind the Scenes
When an organization uses Cloudflare, it hides the original servers. Now, if an attacker will try some attack it will not affect the original servers because they’ll now be directed towards Cloudflare. Eventually, Cloudflare will block the requests protecting the organization.
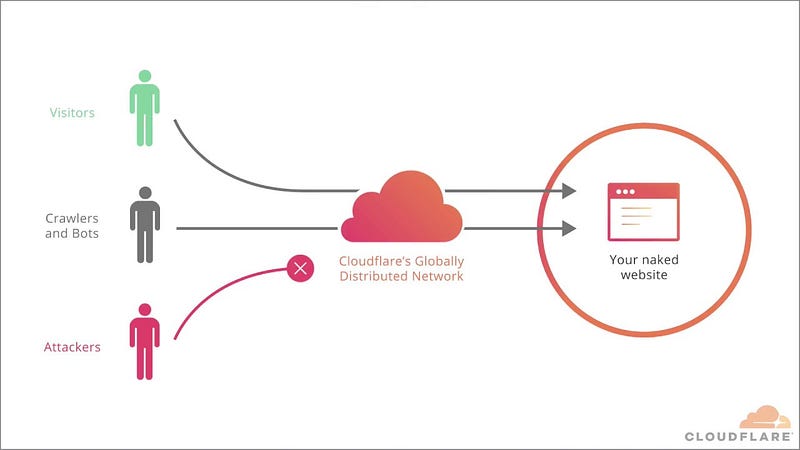
How to bypass Cloudflare?
When you can bypass Cloudflare, you can get direct access to the websites. Direct access means if you’ll try to test for vulnerabilities, there will be no firewall to block you. Here are the ways to do it:
1. Resolvers
This is the most common approach where you bypass using other methods of protection used by the organization. If your target has an SSL certificate, then it would be registered in the Censys database. Choose “Certificates” in the select input, provide the domain of your target, then hit <enter>. Click on every result to display the details and, in the "Explore" menu at the very right, choose "IPv4 Hosts". You should be able to see the IPs of those certificates.
2. Subdomain Trick
Many times organizations don’t configure Cloudflare properly. They keep their main domain on Cloudflare address, but subdomains point to real IPs. For this trick, find subdomains of the domain, you can use this article for finding subdomains and then
ping <yourtarget> -- the response will be like -- Reply froom <IP address>: bytes=32 time 260ms TTL=513. Mail Servers
You know what Cloudflare doesn’t handle MX records. Like I shared in the last article that MX records are the Mail Server records, so it is possible to find the real IP address of a website by looking at the IP headers. For this method to work, you’ll have to find the registration or forget the password of that website or find some way to get an email from that website. Once you get an email from your target, do the following:
- Open it and click on “Show original”. You’ll find this option here in your email in three dots:
- Now, you’ll see a copy-to-clipboard option. Click it.
- Go to email-tracer here and it will show you the IP address of the server like shown below.
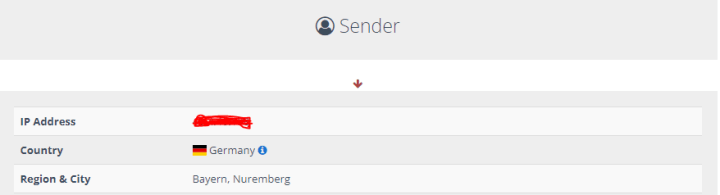
Game Over! Once the right IP gets exposed, the point of using Cloudflare ends, and hence that’s a successful bypass.

There are many tools that state to help you in finding misconfiguration in CloudFlare or help in bypassing Cloudflare. Don’t fall into that trap, instead bypass it with Recon! The more you do manually, the better you’ll understand. If you have more recons for the world to know to bypass this, don’t forget to share in the comments!.
Time to wrap up! Here’s your:
To-Do
- Try these techniques
- Find more recons!
Do this with:CAUTION: You need to make sure that you will not use this information for any illegal purposes. This information is being shared for educational purposes only. If you find something sensitive while practicing this, do not use that information instead inform the website owner as soon as possible.
If you find this interesting, don’t forget to subscribe and I’ll update you every weekend with new content. The next article will start a higher-level — host enumeration. Till then, keep practicing!



